Forty percent of the 600 companies surveyed by the ACC Foundation for 2020 State of Cybersecurity Report: An In-House Perspective suffered a data breach for that preceding year. In fact, the 600 companies averaged 24 cyber incidents in one year!
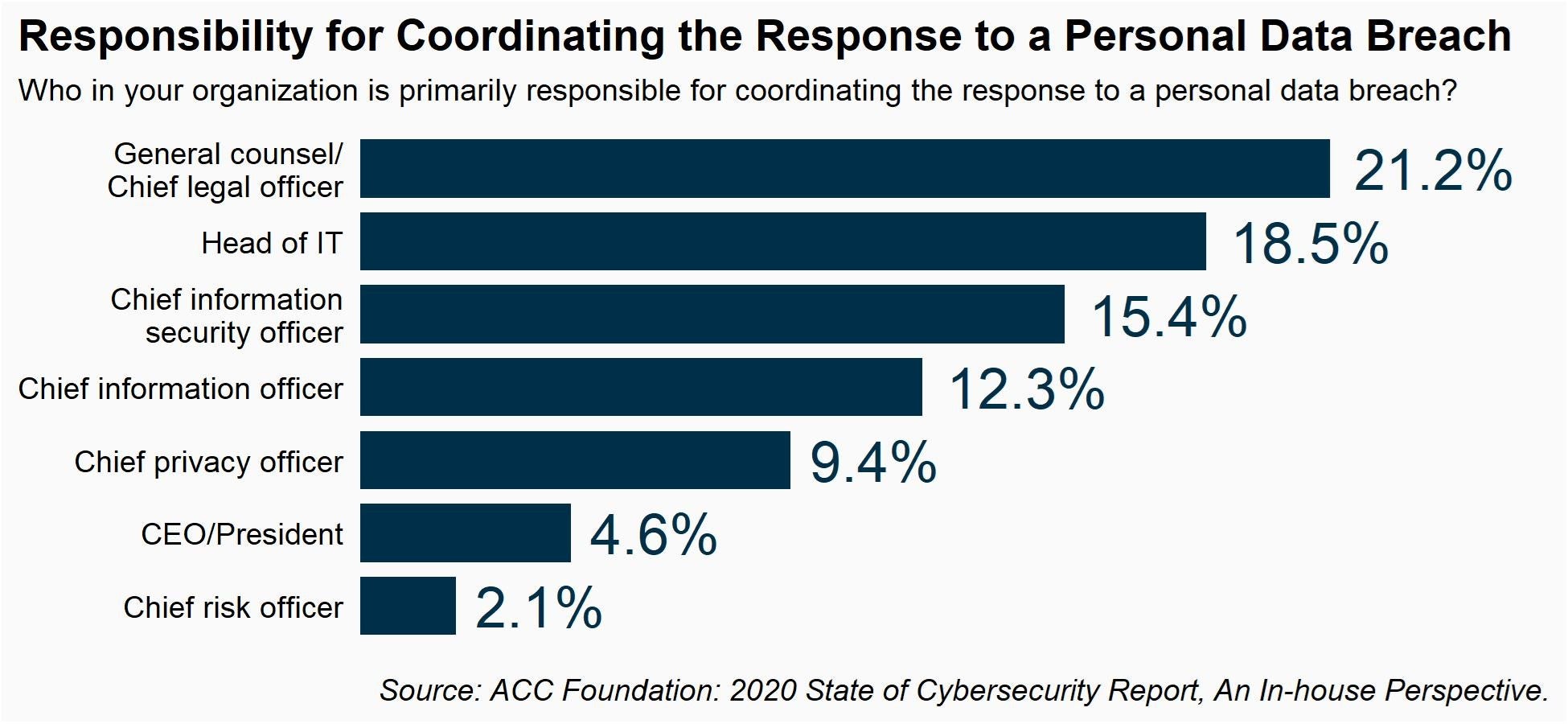
When asked who in the organization is primarily responsible for coordinating the response to a data breach, the most common answer was the chief legal officer (CLO) for 21.2 percent of the companies, up from only 4.6 percent in 2015.
It was not the head of information technology (IT), at 18.5 percent, not the chief information security officer at 15.4 percent, and not the chief privacy officer at 9.4 percent.
With so much at risk, including damage to brand reputation, liability of data subjects, regulatory action, loss of proprietary information, loss of business continuity, and potential executive liability, it is no wonder that CLOs rank cybersecurity as the single most important issue facing their overall business today (see other top findings from the 2022 ACC Chief Legal Officers Survey).
With so much at risk, including damage to brand reputation, liability of data subjects, regulatory action, loss of proprietary information, loss of business continuity, and potential executive liability, it is no wonder that CLOs rank cybersecurity as the single most important issue facing their overall business today.
CLOs play an important role in cybersecurity
CLOs are not only looked to on a reactionary basis (once a data breach occurs, for example), but they often play an integral role in developing the underlying risk-mitigation strategy for the organization. Sixty-one percent of survey respondents say the legal department has a co-equal voice in setting the company’s overall risk-mitigation strategy alongside IT and compliance, and 64 percent of CLOs regularly report to the board of directors on cyber issues or, at minimum, do so on an ad hoc basis.
In 2020, cybersecurity and privacy functions reported to the CLO in 18 percent of companies and this percentage was even higher in the IT, professional services, financial, and insurance industries. Even when the CLO does not directly oversee cyber, they are still either a part of an enterprise-level team that has cyber responsibilities or are in a leadership role on that team in 71 percent of companies.
Even when the CLO does not directly oversee cyber, they are still either a part of an enterprise-level team that has cyber responsibilities or are in a leadership role on that team in 71 percent of companies.
In cases where cybersecurity does report to the CLO, the company’s cybersecurity program tends to take a more proactive risk-based approach (i.e., they search for methods to meet various risks whether or not they are mandated by a regulatory requirement) rather than a more reactive compliance-based approach (i.e., simply following the rules).
In-house counsel dedicated to cybersecurity are increasing
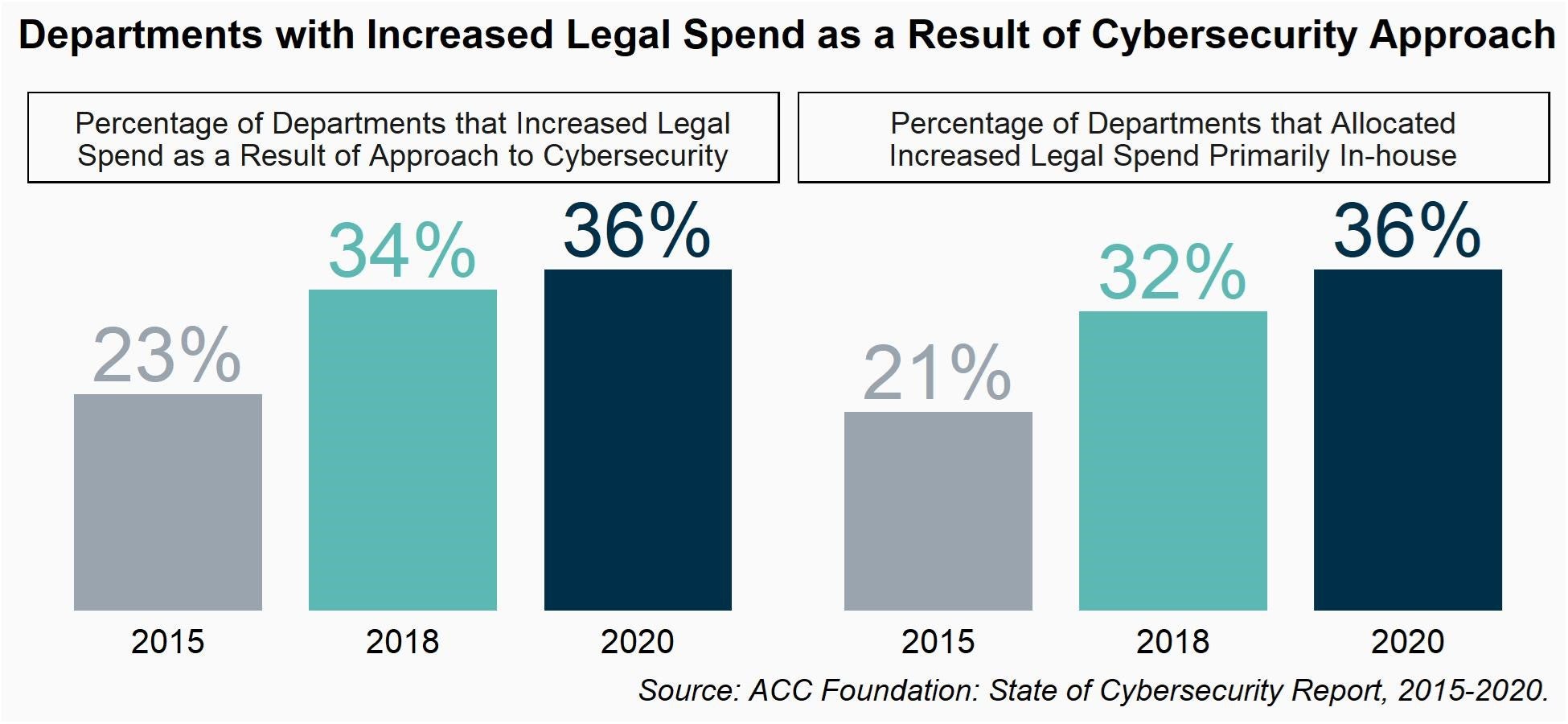
Thirty-six percent of departments say their legal department is spending more as a result of their organization’s approach to cybersecurity and this has been increasing over time with only 23 percent saying so in 2015. Although the majority of spending goes toward outside counsel, the percentage allocated toward inside spend (e.g., in areas like personnel, training, and new systems) has also been increasing over time from 21 percent of the legal budget in 2015 to 36 percent in 2020.
This spending pattern aligns with what we are observing in hiring patterns. In 2020, 18 percent of companies had at least one in-house lawyer with formal responsibilities related to cybersecurity issues, a six-percentage point increase from 2015.
this lawyer (or group of lawyers) has not simply focused on a small number of specific aspects of cybersecurity, but is responsible for coordinating cyberlaw strategy across the entire enterprise.
In larger companies with 50 or more legal staff, this percentage jumped to 44 percent. In 60 percent of those companies, this lawyer (or group of lawyers) has not simply focused on a small number of specific aspects of cybersecurity, but is responsible for coordinating cyberlaw strategy across the entire enterprise, including in areas such as incident response, supply chain concerns, product/service development, labor/employment, regulatory compliance, legislative policy, and PR crises. In most cases, these dedicated cyber lawyers are executive level lawyers.
Tell us about your law department's cybersecurity role
These are just a few of the many findings captured in the most recent iteration of the ACC Foundation’s biannual State of Cybersecurity Survey. Check out the 2020 survey highlights.
The 2022 survey is open for participation from June 14 – 29, 2022, and we want to hear from you! In addition to legal’s role in cybersecurity, the survey asks about cyber policies and practices, your organization’s past data breach experiences, and different aspects of your organization’s approach to risk management, particularly third-party vendor risk management.
For questions or other information, contact: research@acc.com.
Disclaimer: The information in any resource in this website should not be construed as legal advice or as a legal opinion on specific facts, and should not be considered representing the views of its authors, its sponsors, and/or ACC. These resources are not intended as a definitive statement on the subject addressed. Rather, they are intended to serve as a tool providing practical guidance and references for the busy in-house practitioner and other readers.
Disclaimer: The information in any resource in this website should not be construed as legal advice or as a legal opinion on specific facts, and should not be considered representing the views of its authors, its sponsors, and/or ACC. These resources are not intended as a definitive statement on the subject addressed. Rather, they are intended to serve as a tool providing practical guidance and references for the busy in-house practitioner and other readers.




